ArcGIS with WAF v2
Roger Groom & Scott Bennett-McLeish, 25 August 2021
Country: Australia
Akkodis developed and continues to manage a fleet of ESRI ArcGIS geospatial servers for a commercial operator in the lands industry.
The Scenario Akkodis developed and continues to manage a fleet of ESRI ArcGIS geospatial servers for a commercial operator in the lands industry.
The ArcGIS application servers in the customers platform are hosted inside private VPC subnets. exposed through a public internet-facing Application Load Balancer (ALB). Java services and end-user client JavaScript talk directly to services hosted on the ArcGIS servers. As such, there is a need for the ArcGIS servers to be publicly accessible.
ArcGIS servers have an administration facility exposed in the same way services are exposed. This is exposed at:
- https://<hostname>/arcgis/manager
- https://<hostname>/arcgis/admin
It was desirable to have those administration facilities inaccessible to the average user who legitimately has access to other ArcGIS services.
Akkodis architected, implemented and operates this service for its customer as a Managed Services Provider. This work was done in early 2021.
The Solution
An AWS WAFv2 was placed in front of the ArcGIS ALB to block the specific admin URLs. This was added by way of augmenting the existing CloudFormation template responsible for standing up the ALB and ArcGIS servers. The CloudFormation update was such that using conditions the implementation was environment specific.
The WAFv2 was enabled with the following rules:
| Rule | Type | Action |
|---|---|---|
| ArcGisWafRuleBlockAdmin | Custom | Block |
| ArcGisWafRuleBlockManager | Custom | Block |
| AWSManagedRulesCommonRuleSet | AWS Managed | Count |
| AWSManagedRulesAdminProtectionRuleSet | AWS Managed | Count |
| AWSManagedRulesKnownBadInputsRuleSet | AWS Managed | Count |
| AWSManagedRulesWindowsRuleSet | AWS Managed | Count |
The Outcome
In Production, UAT and Test environments the administration pages are now inaccessible outside of the ArcGIS server itself.
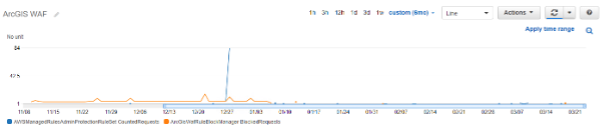
Monitoring showed immediately that there were regular hits to the production ArcGIS administration pages. These regular hits continued for many weeks, then stopped and have not returned. The graph below from CloudWatch metrics illustrates this:
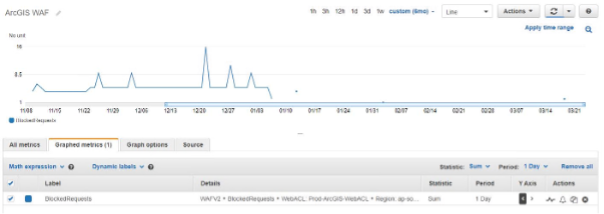
The graph from CloudWatch metrics illustrates regular hits have not returned
While it is unclear if the traffic was ‘legitimate’ or malicious no functionality has been impaired by the introduction of block rules, suggesting it is not legitimate traffic and so a positive outcome being blocked.
Monitoring of the Count metrics for AWS Managed Rules shows there is potential for further improvement.
The below illustrates a spike in counts for the AWS Managed ‘admin’ rule, a spike that does not correlate to the custom rules for ‘admin’ and ‘manager’. This warrants further analysis.