AWS VPC DNS Security: Cisco Umbrella Integration
James Bromberger. 26 August 2021
Country: Australia
The Problem
An electrical energy retailer has started a migration into AWS for its VM based business applications, with Akkodis helping prepare solid, evidence-based business cases and run adoption workshops for the customer since mid-2020.
However, as they commenced this, they wanted to integrate some of their existing security services.
The Scenario
As part of its on-premises architecture, the Akkodis customer uses the Cisco Umbrella DNS resolver and proxy service as part of its protection of outbound requests. This service uses a Cisco-provided recursive DNS resolver which identifies the client systems by the origin source IP addresses in use. The service permits the administrator to classify the target sites being resolved, so to being allow-listed, block-listed, or matching certain categories.
The DNS result returns a different result based upon the target site being safe, unsafe, or somewhere in between:
- Safe sites: the authoritative DNS record is returned to the DNS client
- Unsafe sites: an NXDOMAIN is returned to the DNS client
- Questionable sites: have a DNS result returned that points at a Cisco-operated HTTPS proxy
This Cisco proxy permits clients to connect, make their request, and then scans the response before providing it back to the client system.
This HTTPS request interception requires the client system to have the Cisco Umbrella Root CA as a Trusted Certificate Authority, as the Cisco service will generate a matching certificate on-the-fly for those sites deemed in the ‘questionable’ range.
The Akkodis customer wanted to leverage this protection, but also not make other cloud-based services such as AWS Guard Duty blind to the query traffic being used, and not remove the effectiveness of AWS VPC Endpoints to resolve correctly in each AWS VPC.
The customer turned to the Akkodis AWS Practice in December 2020 to implement a solution…
The Solution
This situation is suitable for Route 53 Outbound Resolver configurations; the templated solution created a pair of outbound Resolver Endpoint interfaces in a pair of private subnets (each in different Availability Zones), with access to the Internet via a NAT gateway. These NAT gateways have static IP addresses, registered with the Cisco Umbrella service.
A Route 53 Resolver Rule was defined to forward queries to the supplied IPv4 addresses for the Cisco recursive DNS resolvers. This Resolver Rule was then shared using AWS Resource Access Manager to various AWS accounts, which in turn then bound the rule to the required VPCs.
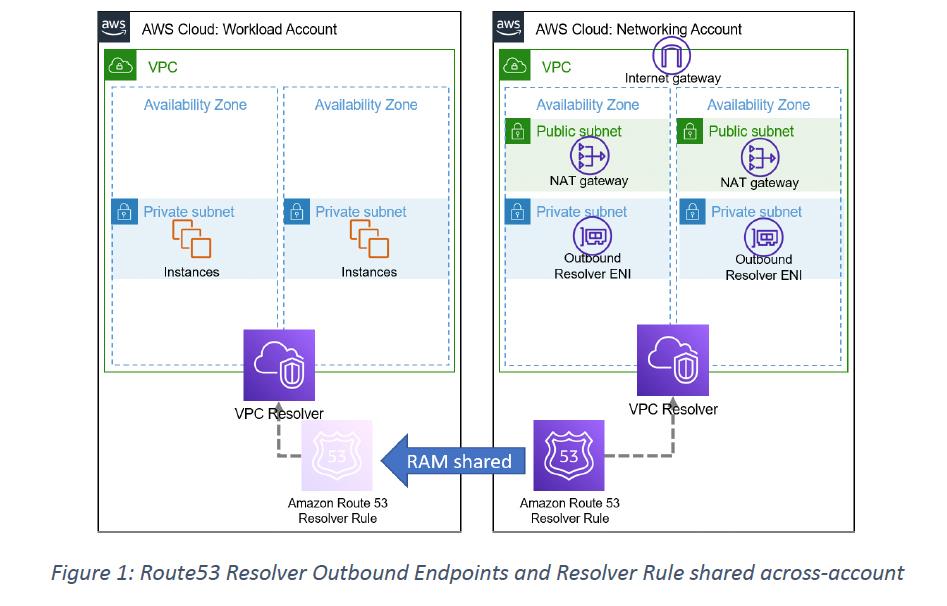
DHCP options within the VPC can be left as pointing at the AmazonProvidedResolver, and VPC Security Groups can remain closed for TCP and UDP port 53. This also prevents any other DNS Resolver being used directly, a technique which is often used by compromised hosts trying to find their command-and-control services.
Akkodis researched and architected the solution, authored the CloudFormation Template to apply this change, and deployed the templates to the customer environments to affect the change.
The Outcome
With this solution in place, the DNS protection of the fleet is visible via the Cisco Umbrellas service (however without the visibility of which instance made the request).
The VPC environment is also further protected from alternate DNS providers being used. DNS results are cached by the VPC-provided resolver, and multiple VPCs do not require VPC Peering or Transit Gateway connectivity between VPCs or Instances for this solution to work.
Furthermore, there are zero customer-managed DNS recursive resolvers deployed that would require maintenance and upgrades over time, further making the service cost effective, scalable, and reliable.
As at April 2021, Akkodis continues to assist this customer on its journey to the AWS Cloud, helping port serverless application, and migrate traditional workloads into the EC2 environment.